What is Single Sign-On (SSO) and How Does It Work?

Single Sign-On (SSO) authentication is a technology that enables a user to authenticate just once and then allows that user access to multiple applications and/or services. While this function seems to indicate that SSO is built for user convenience, it’s way more than that. In this guide, we’ll take a closer look at the key concepts surrounding Single Sign-On and how it plays an important role in boosting an organization’s IT efficiency and security posture.
What Is Single Sign-On (SSO)?
Single Sign-On is a centralized authentication method that allows users to access multiple applications and services without having to log into each one individually. When users authenticate through SSO, they just have to submit credentials once. After that, they should be able to access various applications and services.
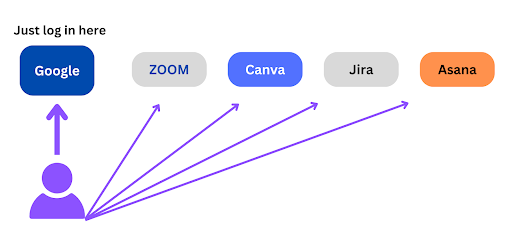
For example, a user can login to Google (e.g. via Gmail) and then gain access to Zoom, Canva, Jira, and Asana, provided of course that the user has accounts in those services. The user only submits its username and password once—when logging on to Google.
People new to SSO sometimes confuse it with Lightweight Directory Access Protocol (LDAP), perhaps because LDAP is also used for authentication. They’re actually built for different purposes. SSO is primarily designed to provide centralized user authentication across multiple applications and services, while LDAP is focused on verifying user identities within a specific directory service or domain. In some cases though, SSO systems leverage LDAP for user authentication against directory services, which is probably also why some people use the acronyms interchangeably.
Advantages and Disadvantages of SSO
So you now know what Single Sign-On is. But why would you use it instead of other authentication methods? And on the flip side, why wouldn’t you? To answer these questions, we need to compare its pros and cons. Let’s start with the disadvantages of SSO.
Disadvantages of SSO
- At the risk of becoming a Single Point of Compromise (SPOC) – SSO’s centralized architecture can become a SPOC. If SSO credentials are compromised, all services and resources protected by those credentials can fall into the wrong hands.
- At the risk of becoming a Single Point of Failure (SPOC) – Similarly, again due to SSO’s centralized architecture, if the SSO system suffers performance issues or becomes unavailable, users may not be able to login.
These are valid concerns. One way to mitigate the SPOC risk is by integrating multi-factor authentication (MFA) instead of just relying on password-based authentication. Not all SSO providers support MFA, so choose one that does. MFA will make it difficult for a threat actor to gain unauthorized access even if it already knows a user’s password.
As with regards to the SPOC risk, you can mitigate it by making sure your Single Sign-On provider has provisions for high availability (HA). Reputable providers usually publish white papers detailing their HA configurations, which may consist of load balancers and redundant infrastructure. You may also inquire about historical uptimes as well as guaranteed availability levels in their Service Level Agreements (SLAs).
Advantages of SSO
Most of the advantages you’ll find below relate to passwords. Although SSO isn’t limited to password-based authentication, password authentication is still the most common method of authentication you’ll find out there. Thus, it will be more relatable if we focus on that kind of authentication. Now that we’ve got that out of the way, let’s proceed with the advantages of Single Sign-On.
- Fosters the use of strong passwords – Password policies usually call for 1) the use of long and complex passwords and 2) the avoidance of password reuse. Because users normally login to multiple applications every day, they find it impossible to maintain separate long and strong passwords AND memorize them all.
As such many users tend to circumvent password policies. They either continue using short and simple passwords, reusing passwords or post passwords where they can easily be seen. All these bad practices can put user accounts and systems at risk.
Since Single Sign-On eliminates the need to memorize multiple passwords, it makes the practice of using long and strong passwords more realistic. Users will find it easier to adhere to password policies this way.
- Boosts productivity – While SSO’s positive impact on user productivity is clear as day—users only have to login once to access multiple applications and services—its impact on your IT team’s productivity is equally or perhaps even more substantial. With SSO, IT staff spend less time dealing with:
- password resets and other password-related issues
- onboarding and offboarding tasks
- Authentication configurations
- Simplifies compliance – Data privacy/protection laws and regulations like HIPAA and PCI DSS have strict requirements for access control and authentication. SSO’s centralized architecture makes it easier for IT admins to implement appropriate controls as well as monitor the effectiveness of those controls.
How Does SSO Work?
Different Single Sign-On technologies have slight differences in the way they work. However, they typically involve three entities:
- A service provider – An entity providing certain services and resources.
- A user – The person who wishes to access those services and resources provided by the service provider.
- An identity provider – An entity that authenticates users
Assuming the user hasn’t logged on yet, the SSO workflow will more or less look like this:
- User connects to the service provider and requests access
- Service provider generates an authentication request for the user and redirects the user to the identity provider
- Identity provider receives the authentication request and asks the user to submit login credentials
- User submits login credentials
- Identity provider looks up its database and authenticates the user.
- If the authentication process succeeds, the identity provider furnishes the user with an authentication token and then redirects the user back to the service provider
- After validating the token, the service provider grants the user access
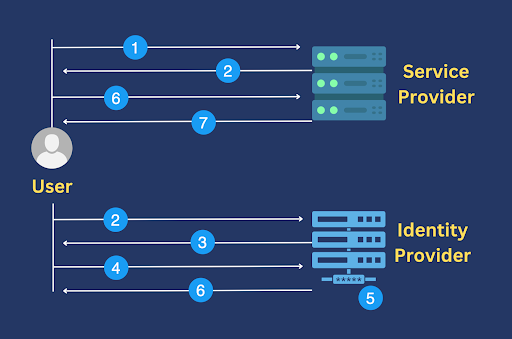
What if the user has already logged on previously and now wishes to access another service provider? That service provider will only have to validate the user’s authentication token. Once the token has been validated, the user can be granted access. No more logs on required.
Obviously, Single Sign-On authentication tokens play a crucial role in letting a service provider grant a user access. Let’s talk about them now.
SSO Authentication Tokens
An SSO authentication token is a data structure or digital credential that’s generated after a user has been authenticated by an identity provider. This token serves as proof that the user has already been authenticated. When the user attempts to access a service, it presents the token to the service provider, which then validates the token’s authenticity. Once the token has been validated, the user is granted access.
The specific composition of an SSO authentication token can vary from one SSO technology to another. That said, a typical token may possess the following attributes:
- Identification – A collection of information about the user’s identity, access privileges, attributes, and so on.
- Security – The token is usually encrypted to protect it from eavesdroppers and tampering.
- Validity period – A prescribed period for which the token can be used. When that period ends, the user may have to re-authenticate.
- Digital signature – The token is usually digitally signed by the identity provider. That signature is used by service providers to validate the token’s origin and authenticity. Only digital signatures from trusted identity providers will be accepted.
SSO Within an Access Management Strategy
Single Sign-On fits perfectly in a comprehensive access management strategy. It works synergistically with other components such as access control, permission control, and activity logs to streamline access management. Moreover, it can be integrated with user behavior analytics and monitoring solutions to further improve security.
SSO acts as the gatekeeper, taking charge of the authentication process. Once a user has been authenticated, access and permission control systems take over. These systems dictate which resources the user is allowed to access and what operations can be performed against those resources.

Furthermore, SSO can be configured to store detailed activity logs of user authentication and access activities. These logs can be ingested into user behavior analytics (UBA) and monitoring tools to detect anomalies and prevent malicious actions. UBA insights can also be used to inform adaptive access policies. For instance, a user’s current risk profile can be used to determine which authentication requirements (e.g., in a multifactor authentication SSO system) should be applied.

Common SSO Types and Configurations
Knowing the different SSO types and configurations is essential to your journey toward SSO adoption. It will help you choose the right technology for your organization. While we won’t be able to cover the various types and configurations in detail in this guide, it would certainly help to know the most commonly used ones.
SAML-based SSO
Security Assertion Markup Language (SAML) is best known for enabling web SSO. It allows users to do single sign-on for multiple web-based as well as cloud-based applications and services. SAML is also good at enabling Single Sign-On across different domains and organizations.
Kerberos-based SSO
Being integrated as the default authentication protocol in Windows, Kerberos-based SSO is most widely used in Windows domains. One of its use cases is in Integrated Windows Authentication (IWA), where Kerberos is used for providing SSO to users accessing web applications in the Windows domain.
Smart card-based SSO
Smart card-based SSO is a more advanced SSO type. It’s a form of multifactor authentication that often combines something the user knows (usually a PIN) and something the user has (the smart card). You would typically use it when accessing applications and services that require a higher level of security.
Conclusion
Single Sign-On authentication simplifies access, strengthens security, and boosts productivity in organizations where users have to log on to multiple applications and services. It does so by reducing log-on to just one through a centralized, secure, robustly-integrated system.
Most SSO solutions still use passwords. Unfortunately, passwords are prone to various attacks such as brute force, credential stuffing, phishing, and social engineering. Although you can augment password-based SSO with another authentication factor to improve security, it’s more convenient and secure to do away with passwords altogether.
At Kelvin Zero, we are going a step beyond SSO by building next-gen authentication and trust solutions to help secure organizations in today’s digital world. With Multi-Pass, we are replacing passwords with enterprise-grade, phishing-resistant passwordless authentication so you can stay one step ahead.
Book a demo today to learn more about Multi-Pass and how Kelvin Zero can help your organization integrate Multi-Pass into your SSO and throughout all of its operations.