Exploring Single Factor Authentication: An In-Depth Overview

Single factor authentication (SFA) is any kind of authentication that only uses one authentication factor. That factor may be something you know, something you have, or something you are. In the early days of digital security, SFA was enough to keep threat actors at bay. These days, however, with the growing sophistication of cyber threats, it’s often risky to rely on a single factor for authentication.
In this article, we’ll define what SFA is, what its strengths and weaknesses are, what different types of SFA are out there, and several other concepts related to single factor authentication. Ready to explore the field of SFA? Let’s begin.
Understanding Single-Factor Authentication
Let’s start by defining what SFA is and how it works.
What is Single-Factor Authentication (SFA)?
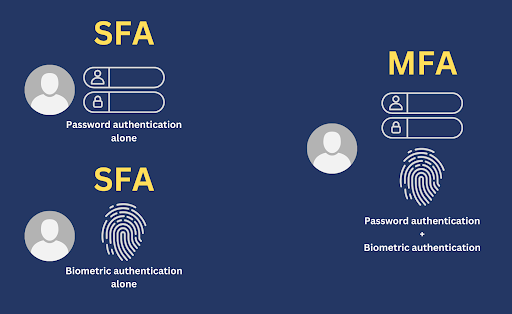
Single-factor authentication refers to a kind of authentication that only uses one factor. The term is used to differentiate it from ‘two-factor authentication (2FA)’, which uses 2 factors, or ‘multi-factor authentication (MFA)’, which uses two or more factors. That brings us to the question, “What are the factors of authentication”? It’s probably easier to explain what they are by giving specific examples.
There are currently three widely used factors of authentication:>
- Something you know, such as your password or passphrase;
- Something you have in your possession, whether physical or virtual, such as a smart card, your SSH private key, your security token, or your phone;
- Something you are, i.e., something based on your biometric attributes, such as your fingerprint, your voice, your face, or your iris.
In other words, an authentication factor is a category of credentials that a user submits when authenticating with a system.
So, going back to our main topic, single factor authentication is a method of authentication that asks you to authenticate using only one particular factor. That could be any of those 3 factors mentioned earlier. But in most cases, the factor used is of the something-you-know kind; more specifically, password-based authentication.
Most authentication systems in the past only used SFA, which usually came in the form of password-based authentication. There was no need to define SFA. It simply existed. But with the continued rise of cyber threats, more and more organizations are starting to adopt 2FA or MFA. So now, there are times when we need to distinguish between 2FA, MFA, and SFA.
How Does SFA Work?
In their most basic form, SFA systems consist of three entities:
- An authenticating system that accepts a particular authentication factor;
- A requesting entity, usually a user but can also be a requesting system (e.g. an application or device) that possesses a credential for that authentication factor; and
- A database of values that match credentials owned by legitimate requesting entities. These values can take the form of:
- Hash values for password-based authentication
- Biometric templates for biometric authentication
- Public keys for public key authentication
- And so on
A typical SFA authentication process follows these general steps
- The requesting entity submits a credential. Depending on the authenticating system used, that credential may be a password, private key, fingerprint, and so on.
- The authenticating system receives that credential and compares it with the values in the database.
- If a match is found for the submitted credential, the authenticating system treats the requesting entity as a legitimate entity and grants it access.
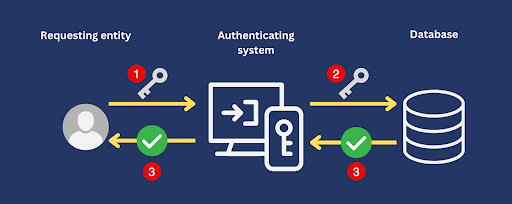
Please note that real-world SFA systems are more sophisticated. The steps outlined above represent a simplified version of SFA.
Strengths and Advantages of Single Factor Authentication
While the use of single factor authentication isn’t advisable, especially in a business setting where confidentiality, integrity, and availability are crucial, it does have some major strengths. Let’s discuss those strengths now.
Note: Despite these ‘strengths’, it’s a bad idea to continue using SFA. Your data and other IT assets will be more secure with 2FA or MFA.
Easy to use – Since an SFA system only requires one factor, users will encounter less difficulty learning and using it. In fact, if that factor is password-based authentication, users can use it straight away.
Easy to implement – Your IT team or whoever is tasked to set up your authentication system won’t have to study, set up, and configure multiple authentication technologies. In most cases, that SFA system would already be included in whatever system it’s designed to protect.
Allows quick access – A multi-factor authentication system would typically require a user to perform multiple steps before granting access. In contrast, a SFA system would only require one step.
Low overhead – A 2FA or MFA system would require two or more additional technologies. Sometimes, those additional technologies aren’t built into the system they’re meant to protect. That means you’d have to spend more to acquire, set up, and implement those technologies. SFA’s simplicity makes it cheaper to implement.
Types of Single-Factor Authentication
There are many types of single-factor authentication. But to give you a solid grasp of this topic, here are three widely used types.
Password-based authentication

Easily the most commonly used type of SFA, password-based authentication is familiar to practically everyone. Password-based authentication entails entering a secret password that (supposedly) only the user knows. If the password matches the value associated with the user in the authentication system’s database, that user is instantly granted access.
For password authentication to work as intended, passwords must be kept secret. Users must not share their passwords to anyone, nor should users post them where they can easily be seen. In addition, passwords should be hard to guess. A password like “asdf” or “password” is easy to guess and would do little to stop a hacker from taking over an account. Passwords must also be changed regularly to minimize risk in the event of a data breach that exposes passwords.
When used alone, password authentication can’t offer sufficient protection against skilled and determined threat actors. First of all, a short password can easily be cracked by what’s known as a brute-force attack. Secondly, even long and strong passwords can be compromised through social engineering attacks or credential stuffing attacks.
Biometric authentication

Biometric authentication leverages unique patterns in certain biological attributes to verify a user’s identity. Apple’s Face ID and Touch ID are popular examples of biometric authentication systems. Biometric authentication can come in the form of:
Fingerprint scanning – Uses unique patterns in a user’s fingerprint;
Facial recognition – Uses unique features in a user’s face;
Iris scanning – Uses unique patterns in a user’s iris.
While biometric authentication can be a very accurate method of user identification, it’s also dependent on certain factors. This includes the quality of the biometric data captured, the reliability of the biometric sensors, and certain external factors. For instance, facial recognition can be negatively impacted by poor lighting.
Biometric authentication also raises security and privacy concerns. Our biometric features can’t change. So if our biometric data is compromised, we could permanently lose our identities to identity thieves. Some biometric authentication systems, such as facial recognition, can also be abused by surveillance states. Authoritarian governments can easily conduct massive surveillance once they’ve captured their citizens’ biometric data.
Hardware tokens

Hardware tokens are physical devices that are associated with a particular user. Examples of hardware tokens include:
- Key fobs – tiny devices that give you access by generating a random number.
- Smart cards – Cards with embedded chips that communicate with a card reader and give you access once the chip is inserted or in contact with the reader.
- USB tokens – USB devices that you plug into a computer for authentication.
Hardware tokens are ultra-portable devices, which is one of their biggest advantages. Depending on the type, these tokens can be attached to your keychain, inserted into your wallet, or placed in your pocket. That said, their biggest strength can also be their biggest weakness. Their ultra-portability makes them susceptible to getting misplaced or stolen.
Single Factor vs. Multi-Factor Authentication
Organizations are gradually shifting from SFA to MFA. To understand why, you need to understand how SFA compares with MFA. You already know what single factor authentication is, so let’s take a closer look at MFA this time. Multi-factor authentication combines two or more SFA systems. In a multi-factor authentication system, a user would have to go through each factor before that user is granted access.
So, for example, if you combine a password authentication system and a biometric authentication system, the user would have to submit a password AND undergo a biometric scan. If the user fails to authenticate with one factor, access will be denied. This multi-layered approach to authentication gives MFA the upper hand when it comes to security.
Best Practices for Implementing Single-Factor Authentication
As there are several types of SFA, best practices can differ from one type to another. In the following sections, we’ll outline the best practices for each SFA type we talked about earlier.
Password-based authentication best practices
Password-based authentication best practices revolve around securing passwords. Here are two ways to do that:
Implement strong password policies. These policies include:
- Using long passwords. Generally speaking, longer passwords are harder to crack
- Using complex passwords. >Complex passwords typically consist of a mix of uppercase and lowercase letters, numbers, and special characters (e.g., $%#@). Alternatively, you can also use passphrases like “mountain river sunset today”, as they’re hard to crack but also easier to recall.
- Changing passwords regularly. This will prevent threat actors from breaking into an account indefinitely using stolen passwords
- Avoiding password reuse. Password reuse is susceptible to credential stuffing attacks. Every user must use a unique password for each of their accounts.
- Use password managers. Password managers are tools that simplify the task of implementing strong password policies. These tools have, for instance, password generators that can automatically generate long and complex passwords with the click of a button. They also prevent you from reusing passwords by eliminating the need to remember long, complex passwords for every single account. All you need to remember is a master password.
Biometric authentication best practices
Biometric authentication best practices are different from password authentication best practices. Whereas the latter focuses on securing your credentials, i.e., your passwords, the former isn’t as concerned with those. In biometric authentication, your biometric features serve as your credentials. It would be hard to secure those the way you secure passwords. Here are two best practices that are more applicable to biometric authentication:
- Secure biometric data or templates– These are the values that your biometric features are compared with during authentication. To prevent them from getting altered or stolen by a threat actor, you must ensure that they are stored securely. You can, for instance, protect them with data-at-rest encryption.
- Use fallback authentication methods – In the unlikely event that a biometric authentication system fails to authenticate a legitimate user, an alternative authentication method must be readily available to authenticate that user. Otherwise, the user can be locked out.
Token-based authentication best practices
As in password-based authentication, token-based authentication best practices also focus on securing credentials, i.e., the physical tokens themselves. Here are two best practices for this type of SFA:
- Constantly remind users of token security – As discussed earlier, the ultra-portability of hardware tokens makes them susceptible to getting misplaced or stolen. For this reason, it’s important to educate users about the risks of mishandling and misplacing tokens.
- Implement token expiration dates – Token expiration dates can minimize the risk of token abuse in case a token falls into the wrong hands. Once the token reaches its expiration date, it will automatically become unusable.
Statistics on Single-Factor Authentication
Before we end this guide, here are some statistics related to single-factor authentication that might pique your interest.
- More businesses are shifting from SFA to MFA. According to LastPass’ “3rd Annual Global Password Security Report”, 57% of businesses globally are now using MFA. This is the result of a 12-percentage points jump from the previous year. The next statistic probably explains why MFA adoption is on the rise.
- Use of stolen credentials and brute force attacks are the number one and number three top action varieties respectively for breaches caused by basic web application attacks according to the Verizon 2022 Data Breach Investigations Report. These types of attacks can be mitigated by using MFA instead of SFA.
- The volume of password attacks increased by 74% in just one year, according to the Microsoft Digital Defense Report 2022. If organizations keep using SFA, most of which are password-based authentication, they will likely fall prey to these types of attacks.
Conclusion
Although organizations are clearly shifting gradually away from Single Factor Authentication, SFA continues to be a popular authentication option. Its speed, simplicity, and affordability continue to attract organizations that don’t feel the need to prioritize security. But for those who value the security of their data, applications, and systems, an authentication system that relies solely on a single factor is just too risky.
You don’t have to sacrifice security for the sake of simplicity. Check out Kelvin Zero’s Multi-Pass, an authentication solution that brings you the robust protection of Multi-Factor Authentication, the simplicity and ease-of-use of Single Factor Authentication, and the power of passwordless authentication.
Book a demo today to learn more about Multi-Pass and how Kelvin Zero can help your organization integrate trust throughout all of its operations.