Multi-Factor Authentication: Comprehensive Guide

Multi-Factor authentication (MFA) is any kind of authentication method that uses two or more authentication factors. Authentication factors may include something you know, something you have, and/or something you are. The use of MFA is now crucial, especially in business environments where unauthorized access can lead to costly data breaches and other business-impacting security issues.
Findings from the Verizon 2023 Data Breach Investigations Report show that stolen credentials are the number one route attackers take to access an organization.This underlines the importance of strengthening your authentication controls. Multifactor authentication plays a big role in helping you strengthen those controls.
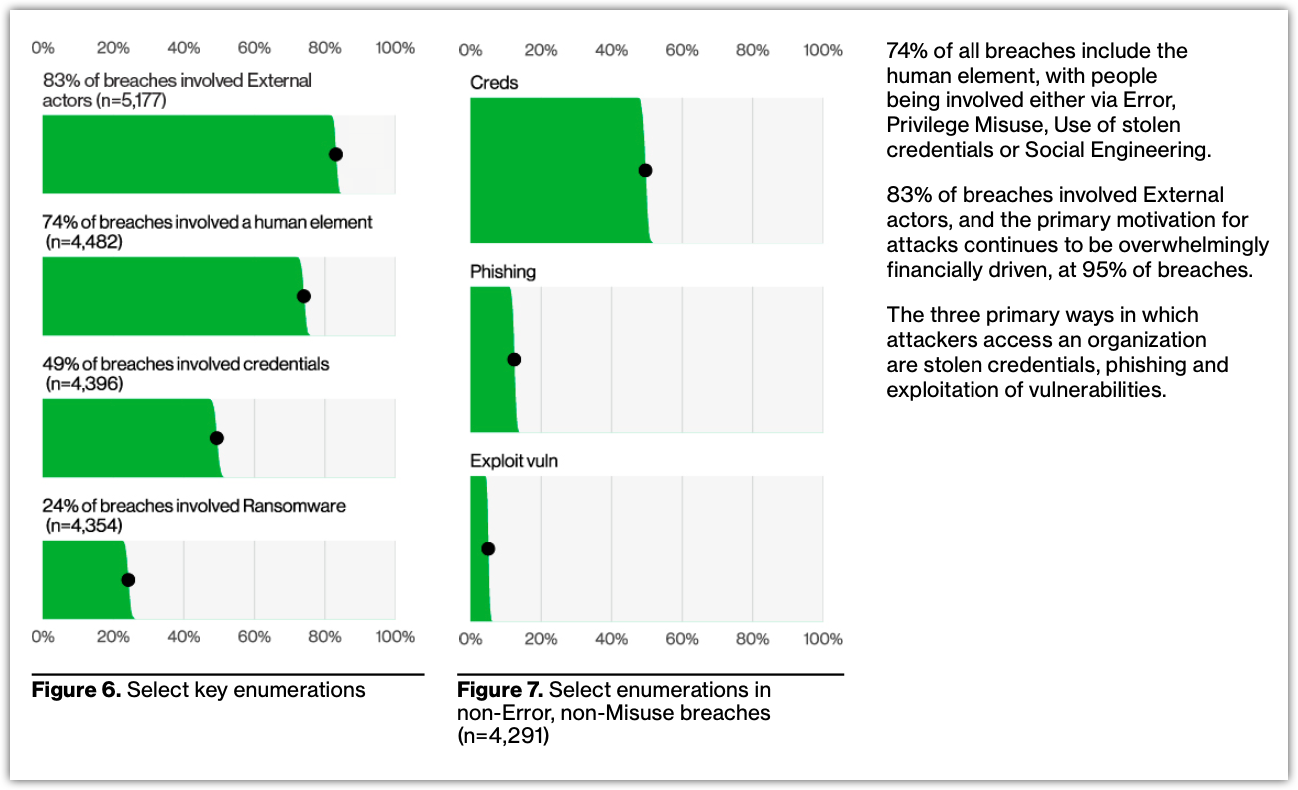
Source: 2023 Data Breach Investigations Report
In this comprehensive multi-factor authentication guide, we will take a deep dive into various aspects of MFA. We will talk about the different factors of authentication, ways of implementing MFA, challenges and considerations when adopting MFA, and other related concepts. When you are done with this guide, you will gain not only a more in-depth understanding of MFA but also a better appreciation of its importance in business environments.
Understanding Multifactor Authentication
Let’s start by defining what multifactor authentication is, the different factors of authentication, and the benefits of adopting MFA.
What is multifactor authentication?
Multi-factor authentication is any kind of authentication that combines two or more factors. More often than not, the first factor is password-based authentication, as it is already widely used. Organizations typically combine password authentication with other methods of authentication such as token-based authentication, biometric authentication, and public key authentication, to mention a few.
The idea is that, by adding more factors of authentication, you will be making it more difficult for an attacker to gain unauthorized access. If one factor fails, the other factors can still provide additional layers of protection.
To understand this definition better, let’s dive deeper into the factors of authentication.
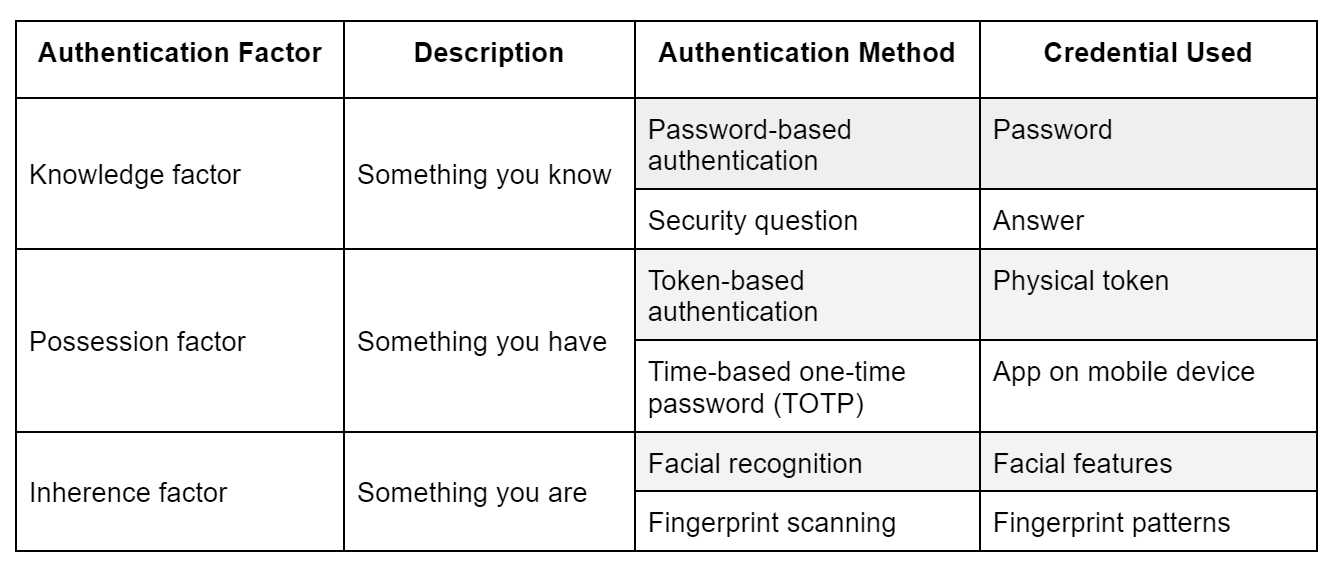
Types of Factors in Multifactor Authentication
There are currently three factors of authentication:
- Knowledge factor – The credential used for authentication is something you know, like a password, an answer to a question, or a PIN code.
- Possession factor – Here, the credential used for authentication is something you have, like a physical token, a smart card, a digital factor (i.e. an SSH key or password manager), or your smartphone.
- Inherence factor – The credential used for authentication is something you are or something inherent in you, like your facial features, fingerprint patterns, or iris patterns.
It’s important to distinguish factors of authentication from methods of authentication. So, for example, while password authentication and PIN-based authentication are different methods of authentication, they’re both based on what the user knows. Thus, if you use these two methods, you’ll only be employing one factor of authentication, and will not be employing MFA.
While using two methods of authentication of the same factor is still more secure than just one method, it typically won’t be as secure as a multifactor system. For instance, it’s easier to steal two knowledge-based credentials like a password and a PIN than to steal a password and say a physical card. The attacker would have to be physically present to steal that card. A password and a PIN, on the other hand, can both be acquired through non-physical means, such as a social engineering attack.
Benefits of Multifactor Authentication
A multifactor authentication system will naturally require users to go through more hoops than a single-factor authentication (SFA) system like password authentication. Being more complex, an MFA system will also be generally more expensive to build and maintain. But why are organizations shifting to MFA? Here are some key reasons:
- Improves security – This is the biggest reason. As mentioned earlier, MFA will make it more difficult for an attacker to gain unauthorized access to a system
- Mitigates password-related risks and vulnerabilities – Although widely used, password authentication is riddled with vulnerabilities. That’s why threat actors exploit it through a range of attacks like brute force, phishing, social engineering, dictionary attacks, man-in-the-middle, and credential stuffing. By adding more methods and factors of authentication, the weaknesses of password authentication can be minimized substantially. Even if an attacker beats password authentication, other factors can prevent the attacker from breaking in.
- Boosts user confidence – With proper education on the advantages of MFA, users will gain more confidence in the security of their data.
- Helps in regulatory compliance – Certain laws and regulations like PCI DSS explicitly require the use of MFA. Thus, MFA adoption can result in regulatory compliance.
- Reduces the risk of a data breach and the costs associated with it – The 2023 Cost of a Data Breach Report has identified Identity and Access Management (IAM) as a key factor in reducing the potential cost of a data breach. MFA happens to be a key component of IAM, helping reduce potential data breach costs.
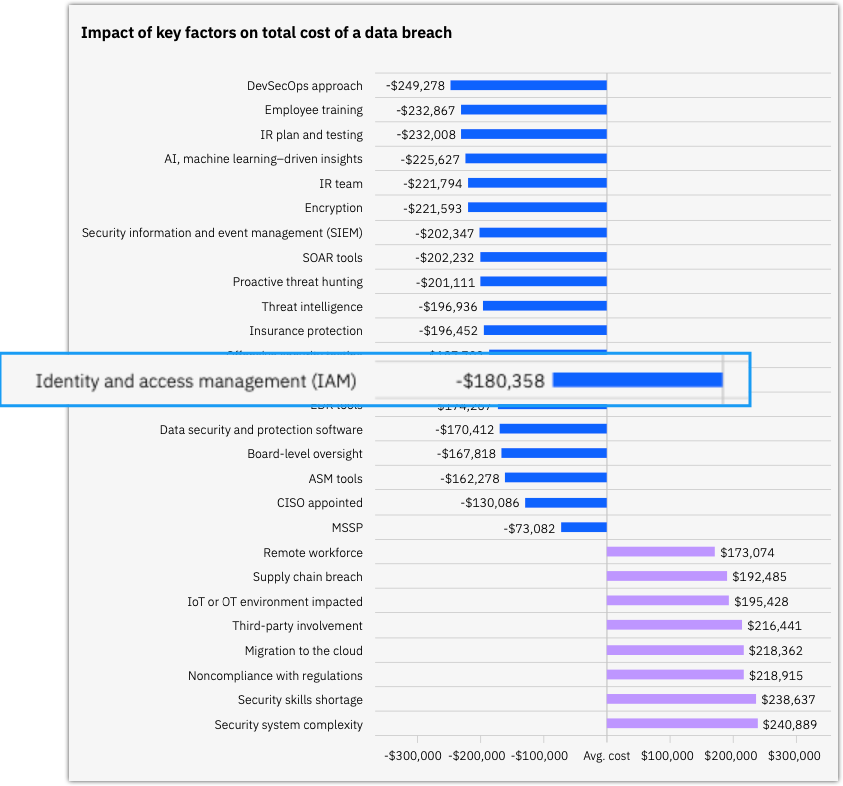
Source: IBM-Ponemon 2023 Cost of a Data Breach Report
Implementing Multifactor Authentication
Most modern systems already have multi-factor authentication capabilities built-in. In most cases, you just need to enable it.
Enabling Multifactor Authentication for Online Accounts
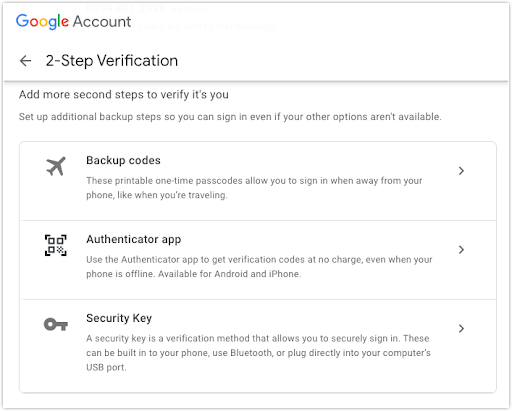
In online services like email, social media, online banking, e-commerce, and so on, you often just need to go to your account’s security settings and enable it there. Other services, like Google for instance, offer additional options like the ones shown below.
One of the most popular options is to use an authenticator app like Google Authenticator or Microsoft Authenticator. These are mobile apps that continuously generate TOTPs that can be used to login to specific apps or services within a given time frame, like 30 seconds or 1 minute. You would typically enter these TOTPs in addition to your username and password before you’re granted access. The numbers you see in the screenshot below are TOTPs for the corresponding blurred applications on top of them.
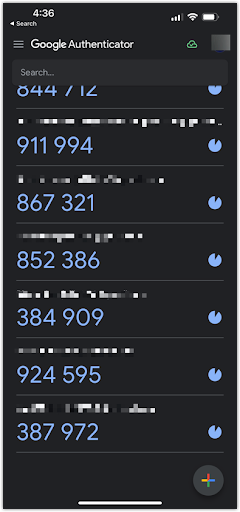
Multifactor Authentication in Mobile Devices
In mobile devices, multi-factor authentication usually comes in the form of a password, a PIN or passcode, and, if the device supports it, a biometric method of authentication. In iOS devices, for example, you can use FaceID, which is iOS’ facial recognition software. In some devices, you may also have to pass through two initial factors of authentication. Additionally, for most devices, once your phone has been associated with you, you will be required to submit one factor of authentication, like a facial scan or a passcode, moving forward.
Incorporating Multifactor Authentication in Enterprise Environments
While MFA can certainly be employed for personal use, its adoption is more important in enterprise environments, where the cost of an account takeover or a data breach can amount to millions of dollars.
When you implement MFA in an enterprise setting, you’ll need to take into account certain factors. Aside from cost, you’ll also need to consider the following for your MFA deployment:
- Compatibility – Is it compatible with existing systems in your IT environment?
- Scalability – How well can it support a large and growing population and IT infrastructure?
- User experience – How easy is it for users to learn and use on a daily basis?
- Support and maintenance – How skilled and accessible is the tech support team?
These are a few of the questions you will need to consider before procuring an MFA solution.
Addressing Challenges and Considerations
The questions raised earlier are pretty common. Here are some ways to address them.
User Acceptance Challenges
Because a multifactor authentication system normally adds two or more steps in the authentication process, you’re bound to encounter pushback from employees. For members of your organization to buy into your MFA project, you must:
- Explain the risks of relying on SFA.
- Communicate the security benefits and importance of adopting an MFA system.
- Involve all stakeholders in the planning phase.
- Demonstrate the MFA system’s ease of use.
- Conduct training to ensure a seamless onboarding process.
Interoperability and Integration Issues
Interoperability and integration issues can cause serious downtimes and derail your MFA project. That said, these issues are more difficult to fix if they’re discovered after you’ve already rolled out your MFA system into production. To avoid these issues, you must address them right at the planning stage.
- Involve IT teams, application owners, system administrators, and other stakeholders in the planning phase.
- Assess your current IT infrastructure. Identify the systems, applications, and services that will be affected by the MFA integration.
- Select a compatible MFA solution.
- Evaluate APIs that will be used for integration.
- Conduct compatibility testing.
- Maintain up-to-date documentation.
- Monitor, test, and tweak.
Balancing Security and User Experience
How your end users feel about your MFA system is crucial to your project’s success. If your users find it too tedious and time-consuming, some of them will look for ways to circumvent or disable it. This will defeat the purpose of your MFA project. Worse, if you’re not aware of these circumventions, you’ll be lulled into a false sense of security.
It’s therefore imperative to strike a balance between security and user experience (UX). Your MFA solution must not only be very secure, but it must also have a great UX. This is exactly why you must involve all stakeholders in the planning phase. You’ll be able to solicit useful comments and suggestions regarding UX.
Advanced Topics in Multifactor Authentication
Multifactor authentication technology is still evolving. MFA vendors continue to develop solutions that not only provide better security but also better UX.
Biometric Authentication in Multifactor Authentication
Biometric authentication is perhaps one of the most convenient methods of authentication. You don’t have to remember or deliberately carry any credentials. The credential is already inherent to your body. Two cutting-edge technologies in this field are iris recognition and voice recognition.
Iris recognition authenticates by scanning unique patterns in the ring-shaped region surrounding the pupil of our eyes. Voice recognition, on the other hand, compares vocal features such as pitch, tone, and speech patterns.
Adaptive and Risk-Based Authentication
Adaptive and risk-based authentication takes into account various conditions before challenging the user with an appropriate combination of authentication factors. Adaptive authentication, by itself, adapts to various contextual factors. The adaptability becomes risk-based if the authentication system factors in risk.
Let’s take the case of a user attempting to log in remotely to a company-managed VPN. An adaptive risk-based authentication system can take into account the user’s IP address, location, and device. If the user is logging in from home or from a branch office, the authentication system might require just SFA because it’s less risky. But if the user is logging in from somewhere else, say a hotel lobby, the system might require additional credentials from other factors of authentication because the risk of say a man-in-the-middle attack is higher.
Emerging Trends in Multifactor Authentication
As with other areas in IT, MFA is now also being “AI/ML”-ized. That’s actually a good thing. Artificial Intelligence/Machine Learning can greatly improve the accuracy and speed of certain MFA solutions, like those equipped with adaptive/risk-based technologies. AI/ML is much better at analyzing multiple data points as well as subtle patterns and behaviors. This can help identify potential security threats and sophisticated fraud attempts.
SFA vs 2FA vs MFA
By now, you should be able to tell the difference between multifactor authentication and single-factor authentication. How about multifactor authentication and two-factor authentication? If there’s any confusion left, let’s get it out of the way.
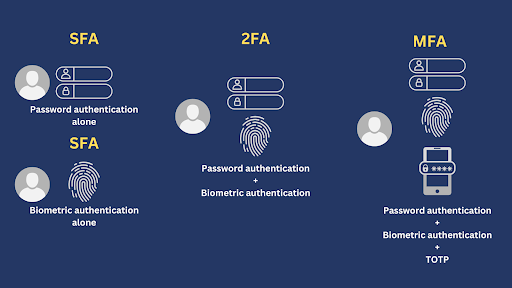
Multifactor Authentication (MFA)
Again, as we’ve said earlier, multifactor authentication is a kind of authentication that involves two or more authentication factors. For example, the MFA system in the diagram above consists of:
- Password authentication (Something you know)
Biometric authentication (Something you are)
TOTP (Something you have)
Two-Factor Authentication (2FA)
2FA is just a subset of MFA. Yes, all 2FAs are MFAs. More specifically, it’s a kind of multifactor authentication that only consists of two factors. For example, the 2FA system in the diagram above consists of:
- Password authentication
- Biometric authentication
Single Factor Authentication
This is the simplest type of authentication. It only consists of one factor. For example, in the diagram above, password authentication and biometric authentication are different types of SFA. Note that, unlike in the 2FA example, password authentication and biometric authentication are used separately.
Best Practices for Multifactor Authentication
Multifactor authentication can provide a very strong level of protection to your IT infrastructure as it can thwart threat actors who aim to gain unauthorized access. That said, it’s still important to exercise best practices to ensure the effectiveness of your MFA system. Here are some tips you can apply.
Keep Authentication Factors Strong and Secure
Each authentication factor plays a critical role in providing an additional layer of protection. It’s therefore important to ensure that each factor is optimized for maximum security. For instance, if one of those factors is password authentication, you must enforce strong password policies. Similarly, if the other factor is TOTP, you must ensure users never leave their phones lying around, especially with the screen unlocked.
Periodically Check and Improve MFA Configurations
MFA settings must be checked regularly to see if they are still appropriate for the current state of your organization and the cyber threat landscape. For instance, you must take into account new hires, new positions, and recently departed employees. To adapt to these changes, you must add, reassign, or revoke credentials and authentication factors.
Educate Users About The Purpose of Multifactor Authentication
Even the most robust MFA system can be ineffective if users don’t cooperate. For instance, barring biometric authentication, if users continue to share credentials, your MFA system will be useless. Constantly educate users about the importance and purpose of MFA. Better yet, instill a security-conscious mindset and culture. Once security becomes second nature, your MFA system—and your other security systems for that matter—will be worth the investment.
Monitor Your Multifactor Authentication System
Despite being highly secure, MFA systems can still be circumvented, abused, or broken. So as not to be caught off guard, constantly monitor user accounts for suspicious logins. If you find anything suspicious, don’t hesitate to investigate.
Conclusion
Multifactor authentication has now become a critical component of any cybersecurity program. Its effectiveness in keeping threat actors out of your systems makes it an invaluable tool in maintaining a robust security posture, preventing data breaches, and adhering to regulatory compliance mandates.
One of the biggest barriers to MFA adoption, however, is its perceived usability and interoperability challenges. A quick introduction to Kelvin Zero’s Multi-Pass can change that perception. With Multi-Pass, Kelvin Zero is replacing passwords with enterprise-grade, phishing-resistant passwordless MFA so critical organizations can stay one step ahead. Book a demo today to learn more about Multi-Pass and how Kelvin Zero can help your organization integrate trust throughout all of its operations.